No matter the size or shape of your site, there can always be vulnerabilities present that could be exploited by cybercriminals.
From sprawling campuses to small office spaces, any workspace that relies on a network is susceptible to cyberattacks. Spotting risks associated with vulnerabilities before it’s too late is essential to avoiding significant costs in repairing any damage and downtime, as well as protecting your business from reputational damage and future business. CyberScope from NetAlly is the world’s first comprehensive, handheld cybersecurity tool which assesses the security of the access layer of site networks via complete visibility into endpoints and potential vulnerabilities. The network access layer enables networks to be versatile, scalable and resilient, but also presents a large target for cybercrime.
Why use CyberScope for Site Assessments?
Network Segmentation Validation
Isolating different network functions makes it more difficult for cybercriminals to move laterally and gain access to sensitive data, making it an essential layer of defence. CyberScope’s AutoTest feature ensures validation of the proper provisioning of your access networks,Wi-Fi or wired, at the touch of a button.
Wired
By using VLANs (virtual local area networks), you can segment different applications even if they are on the same physical network. CyberScope enables AutoTest profiles to be created as native (untagged) or configured to join a specific VLAN. Wired profiles also allow the spoofing of MAC addresses and 802.1X authentication, including 14 different EAP types.
Wi-Fi
Each SSID (service set identifier) represents a different network in Wi-Fi access and is often mapped to its own VLAN. A Wi-Fi profile enables specification of the SSID and associated authentication including the new 6GHz band, Wi-Fi 6E and WPA3, as well as legacy authentication such as WEP and WPA. In addition to this, further SSID validation is possible by supporting band (2.4, 5, 6GHz) and BSSID steering.
Multiple Network Validation
Multiple tests can be grouped together to simplify comprehensive access testing of complex segmented networks to a single button press. This will result in either pass/fail/warning to further deskill access validation. CyberScope’s AutoTest feature includes Nmap integration which allows for in-depth auditing of networked endpoints. This includes open TCP/UDP ports, firewall blocking or checking for broadcast services such as Alexa, Google Cast, Spotify or AirPnP. Nmap output is automatically graded for repeatable pass or fail assessment.
Network Inventory
Discovery reveals your network infrastructure and topology in detail, exposing all endpoints whether they are wired or Wi-Fi. With CyberScope’s configurable extended ranges, you can discover additional non-local subnets which cover your enterprise, or alternatively restrict network ranges and devices that Discovery should not probe. The device also utilises Nmap in its discovery process to allow additional details such as Service, Version, and OS detection.
All discovered devices and even endpoint manufacturers can be classified as Authorised, Unauthorised, Neighbor or Unknown. It is simple to spot outliers thanks to on-device sorting and filtering. Provisioning and network segmentation can be challenging and error-prone processes. With a clear pass/fail indication, CyberScope can check adequate network segmentation at the point of access for both wired and wireless networks. Additionally, CyberScope may join a VLAN to confirm proper segmentation, check switch ports for proper provisioning, and capture traffic on a particular VLAN for more in-depth examination. High-performance technology in CyberScope ensures complete packet capture at line rate speeds.
Analysing paths is essential to comprehending how devices are interconnected. CyberScope offers detailed wired and wireless port-by-port information about the network path to any device. This is essential while looking for mysterious or malicious devices.
You can create real-time, accurate topology maps to see relationships using the associated Link-Live collaboration, reporting, and analysis platform.

Site Wireless/RF Mapping
As Wi-Fi can penetrate through wires and bricks, it represents a critical threat to security. As there are a number of possible Wi-Fi exploits, it’s essential to know the nature and location of every Wi-Fi device on the network, whether it’s an AP, client or a BLE device.
To pinpoint RF devices there are several methods. For example,for quick single device location, the CyberScope Locate feature will use either the internal omni or the external Directional Antenna. CyberScope can perform a path analysis showing all infrastructure devices, and the connection path between you and the device.
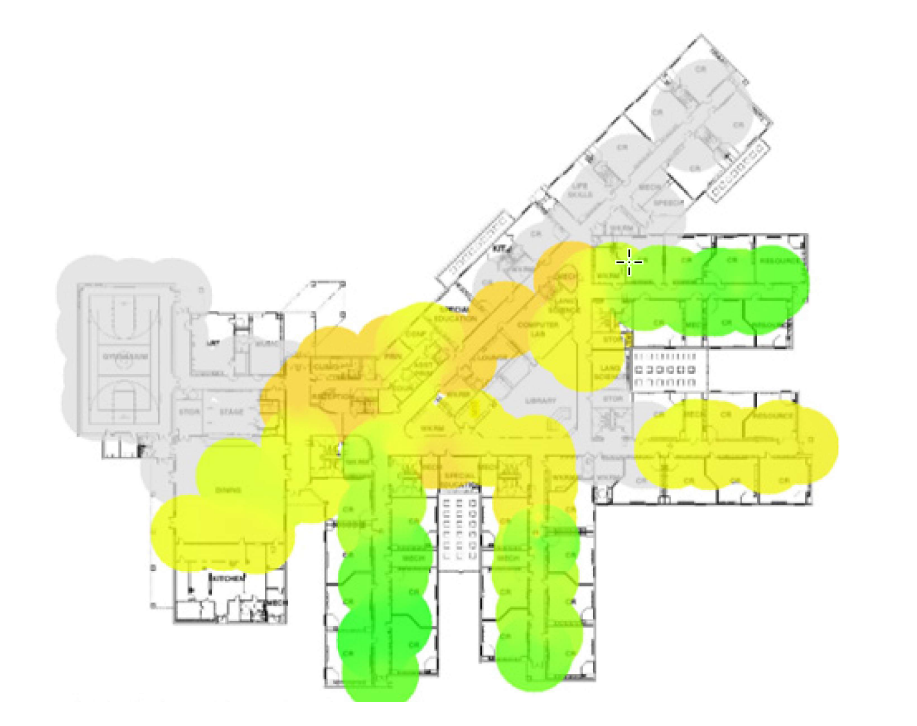
AirMapperTM Site Survey
Any floor plan PDF or image file can be quickly converted into a detailed site RF survey, mapping the presence of Wi-Fi and BLE devices and clients on site using a heat map. CyberScope can simultaneously discover network topologies and perform Nmap investigation of discovered devices when its second management radio is connected to the network.
Integrated Nmap
Nmap technology is fully integrated in CyberScope, providing features for network element probing. This returns critical information about service versions, operating system detection and much more. Built-in features are extendable with over 600 scripts providing deeper details on a per-service or device basis. Custom scripts can also be created and imported into CyberScope.
Benefits of Using CyberScope for Site Assessments
Comprehensive Assessment
CyberScope offers comprehensive access layer site security assessment, analysis, and reporting from a single tool. It actively probes and scans the network to discover endpoints and other components automatically, capturing the interplay. This ensures that all potential vulnerabilities and risks are identified, allowing for a thorough evaluation of the site’s security posture.
Network Vulnerability Detection
CyberScope serves as a network vulnerability scanner, enabling organisations to identify and address potential security weaknesses in their site’s access layer. By conducting regular security testing with CyberScope, businesses can detect and mitigate vulnerabilities before they can be exploited by malicious actors.
Portable and Efficient
Unlike fragile laptops and tablets, CyberScope is a handheld tool that is portable, has all-day battery life, and allows for remote control and collaboration. This makes it convenient for security professionals to conduct site security testing efficiently and effectively, even in remote or challenging environments.
Fast Insights
CyberScope provides fast insights into site networks, offering quick and accurate analysis of the security landscape. This allows organisations to promptly identify and respond to potential security threats, minimising the risk of data breaches or other cyber-attacks.
Conclusion
In short, a site assessment of the access layer should at the very least validate Wi-Fi and wired access segmentation, discover the network inventory, and provide an RF mapping of all wireless devices with their locations.
CyberScope is a crucial tool for any business trying to keep a high level of security. It provides thorough analysis, network vulnerability identification, portability, and quick insights that can assist in finding possible security vulnerabilities before they develop into significant breaches. Site administrators may relax knowing that their access layer and website are secure and complying with regulations thanks to CyberScope. Organisations must employ all available tools to safeguard themselves and their clients as security breaches become more regular and complex in the current digital era. Any organisation that takes cybersecurity seriously needs CyberScope, which offers an essential layer of defence against online











